
Masters in IT :
The course of study is concentrated around the Information Systems discipline.The program is a great opportunity to expand your already existing knowledge of the information technology field and advance your career with better, more meaningful job roles and salary grades.
Students Enrolled
Salary 10 Lacs to 20 Lacs
Online Live class Support
Students got placed
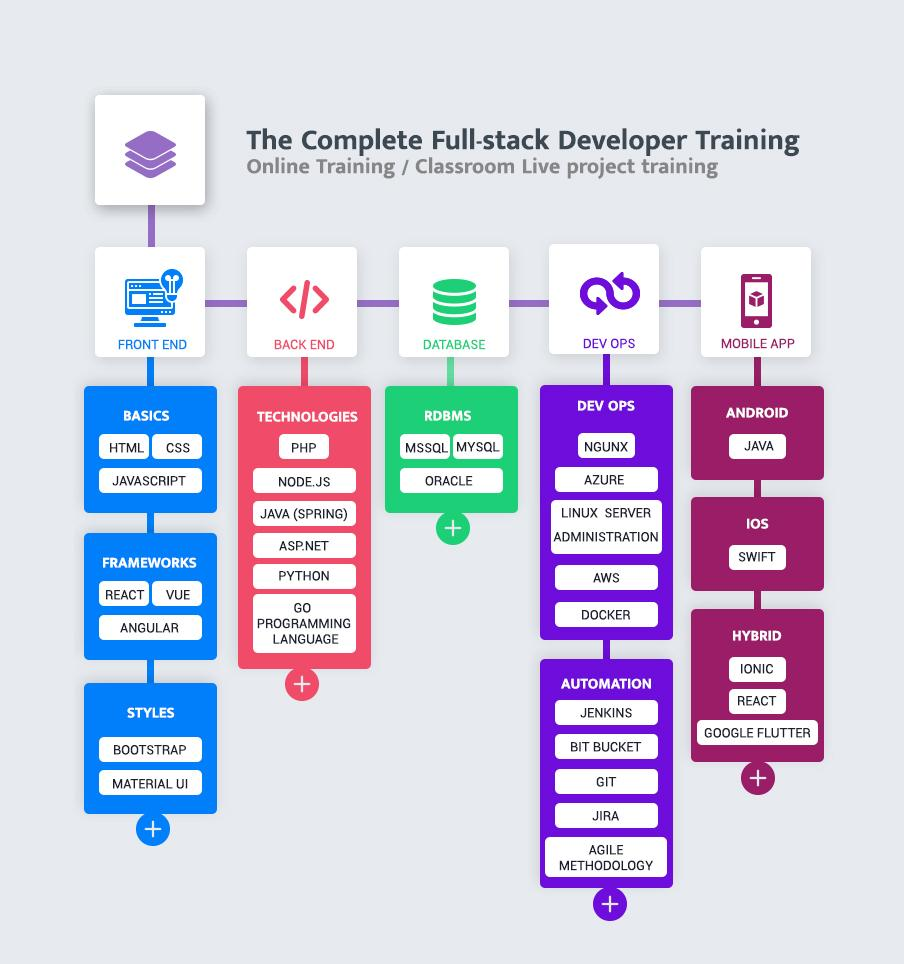
Full Stack Web Development
Full stack development refers to the development of both front end(client side) and back end(server side) portions of web application. Full stack web developers have the ability to design complete web application and websites. They work on the frontend, backend, database and debugging of web application or websites.
In addition to mastering HTML and CSS, he/she also knows how to:
- Program a browser (like using JavaScript, jQuery, Angular, or Vue)
- Program a server (like using PHP, ASP, Python, or Node)
- Program a database (like using SQL, SQLite, or MongoDB)

Masters in Cyber Security
Cybersecurity is the body of technologies, processes, and practices designed to protect networks,
computers, and data from attack, damage, and unauthorized access. Programs in cybersecurity teach
professionals to spot vulnerabilities, fend off attacks, and immediately respond to emergencies.
The cybersecurity job market is growing exponentially and isn’t expected to slow down any time
soon. In fact, a study by Cybersecurity Ventures predicts that there will be more than 3.5 million
unfilled cybersecurity jobs globally by 2021.
The top job titles in the field of cybersecurity are:
- Information security analyst
- Information security engineer
- Network security engineer
- Senior IT auditor
- Information security manager
- Chief Information Officer (CIO)
- Security consultant


RHCSA : Red Hat Certified System Administrator
An IT professional who has earned the Red Hat Certified System Administrator (RHCSA®) is able to perform the core system administration skills required in Red Hat Enterprise Linux environments. The credential is earned after successfully passing the Red Hat Certified System Administrator (RHCSA) Exam (EX200).
Module 01 - Understanding Networks and their Building Blocks
Lesson 01 - Accessing the Command Line
Lesson 02 - Managing Files from the Command Line
Lesson 03 - Getting Help in Red Hat Enterprise Linux
Lesson 04 - Creating, Viewing and Editing Text Files
Lesson 05 - Manage Local Linux Users and Groups
Lesson 06 - Controlling Access to Files with Linux File-system Permissions
Lesson 07 - Monitoring and Managing Linux Processes
Lesson 08 - Controlling Services and Daemons
Lesson 09 - Configuring And Securing Open-ssh Service
Lesson 10 - Analyzing and Storing Logs
Lesson 11 - Managing RHEL Networking
Lesson 12 - Archiving and Copying Files between Systems
Lesson 13 - Installing and Updating Software Packages
Lesson 14 - Accessing Linux File-systems
Lesson 15 - Using Virtualized Systems
Module 02 - Red Hat System Administration II
Lesson 01 - Accessing the Command Line
Lesson 02 - Managing Files from the Command Line
Lesson 03 - Creating and Editing Text files with vim
Lesson 04 - Scheduling Future Linux Tasks
Lesson 05 - Managing Priority of Linux Processes
Lesson 06 - Controlling Access to Files with Access Control Lists (ACL)
Lesson 07 - Managing SELinux Security
Lesson 08 - Connecting to Network-Defined Users and Groups
Lesson 09 - Adding Disks, Partitions, and File Systems to a Linux System
Lesson 10 - Managing Logical Volume Management (LVM) Storage
Lesson 11 - Accessing Network Attached Storage with Network File System (NFS)
Lesson 12 - Accessing Network Storage with SMB
Lesson 13 - How to mount and unmount smb file-system using the command line.
Lesson 14 - Limiting Network Communication with Firewalled
Lesson 15 - Comprehensive Review

